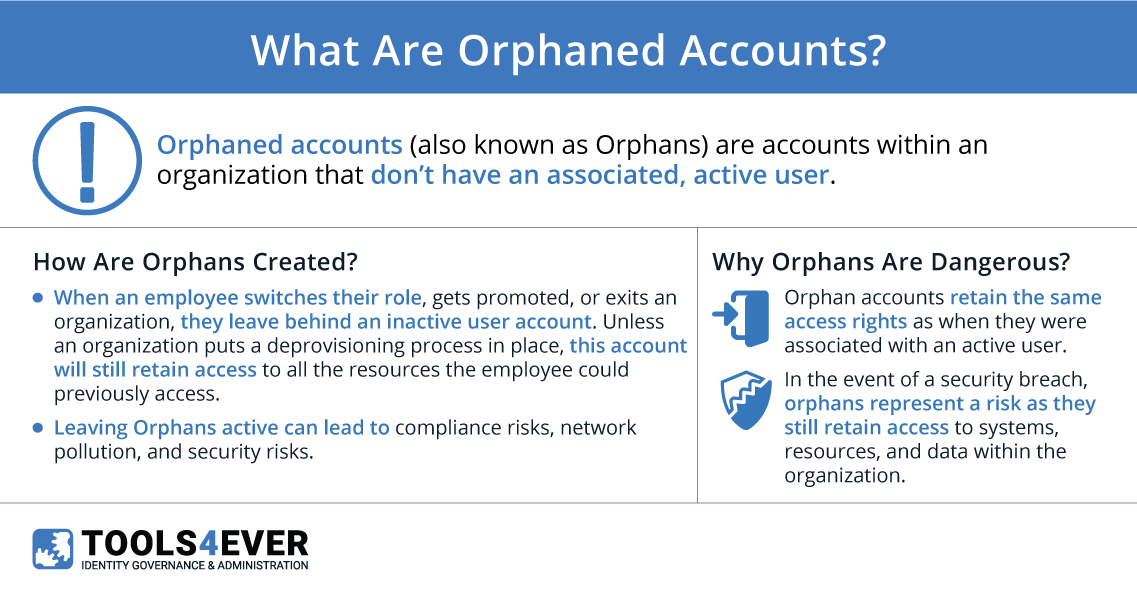
“Orphaned account” is a term describing accounts without an associated, active user.
The term most often refers to network accounts (e.g. Active Directory) associated with former/inactive employees. However, it remains applicable to any type of account that is not actively used. For example, a Google account that is not used by an active employee would still be designated an “orphan”.
Incomplete user account lifecycle management typically leads to the presence, if not proliferation, of orphan accounts. Just as new users must be provisioned upon their hiring, deprovisioning processes must kick off whenever an employee leaves the organization. Though departures are the leading cause, any reorganization, role change, or promotion can lead to unused accounts.
Survey Says
You may be thinking: “I’m sure a few orphan accounts exist on our network, but how bad can it be?” Well, here are some quick stats:
A 2019 Varonis study showed :
- 50% of users are “ghost users” (i.e. orphans)
- 40% of companies have over 1,000 “ghost users”
A 2018 Thycotic report revealed :
- 70% of enterprises fail to discover their network’s privileged accounts*
- 40% of organizations don’t even try to locate their network’s privileged accounts
- 55% fail to remove a privileged account’s permissions after the associated user is removed
*Privileged accounts are those typically granted the most access rights or associated with the most important systems and resources.
What might be most surprising is that these trends are far from new. In 2008, TechCrunch summarized a Symark International survey on the subject following recession-linked mass layoffs. Over 850 security, IT, HR, and C-level professionals responded:
- 42% of organizations do not know how many orphan accounts they have
- 30% do not have a procedure in place to locate orphan accounts
- Roughly 27% state that 20 orphan accounts or more currently exist on their network
- It takes more than 3 days for 30% of those surveyed to terminate accounts after employees or contractors depart; it takes more than 1 month for 12% of those surveyed
- Over 38% have no way to check whether current or former employees used orphan accounts to access information; 15% confirmed that it has happened at least once
Orphan accounts are dangerous. Their presence contributes to network pollution and compliance risks. Further, they retain all the same access rights as when they were associated with active users. Thus, they still provide access to all kinds of systems, resources, and data should an organization suffer a security breach.
i. https://www.darkreading.com/operations/identity-and-access-management/one-third-of-internal-user-accounts-are-ghost-users/d/d-id/1331443
ii. https://solutionsreview.com/identity-management/want-better-identity-management-remove-your-orphaned-accounts/
iii. https://techcrunch.com/2008/12/19/orphaned-user-accounts-are-a-bigger-risk-than-we-realize/
iv. https://www.varonis.com/blog/data-risk-report-highlights-2019/
