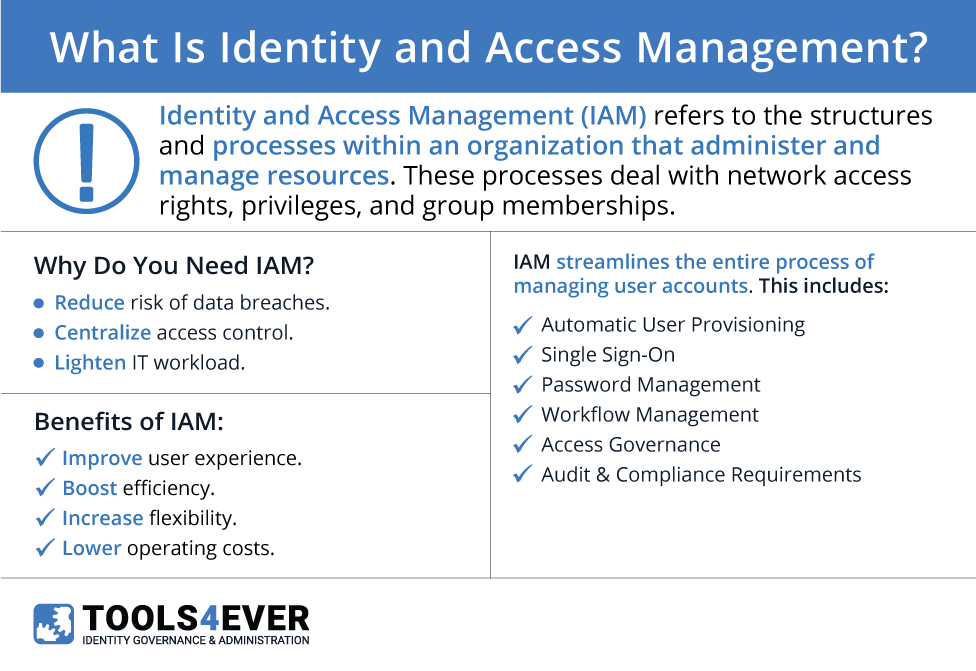
“Identity and access management” (IAM) is the umbrella term for the structures and processes within an organization that administer and manage resources. Predominantly for IT resources, these processes mostly deal with network access rights, privileges, and group memberships (e.g., in HelloID, Active Directory, and Google). These enforce and facilitate the configured access for an organization’s users to systems, applications, data, and more.
Whether cloud-based or on-prem, IAM controls who is granted access to what across your entire IT environment. IAM systems automate and facilitate the execution of the governing structures and processes. These systems help ensure efficient, secure, and compliant operations.
Managing the User Account Lifecycle
IAM systems oversee an organization’s entirety of user account lifecycles for every employee throughout their employment. Comprehensive management requires streamlined, secure processes for:
- Onboarding: Initial creation, provisioning, and user account claiming for new hires.
- “Reprovisioning”: Updating and reviewing user access rights.
- Offboarding: Deactivating user accounts and restricting access when an employee departs the organization.
IAM processes must ensure employees can access the needed resources to work efficiently while minimizing security and compliance risks. User accounts require continual checking and adjustment to account for promotions, reorganizations, new locations, and other role changes.
IAM: Authentication & Authorization
Identity and Access Management governs user access via authentication and authorization. Authentication verifies a user’s identity. Once authenticated, the verified user may use any of the resources their account is authorized to access.
IAM Authentication
Authentication occurs whenever a user attempts to access your organization’s network and downstream resources. The user must verify their identity before being granted entry for security.
Entering credentials at a login prompt remains the most common authentication method. Verified credentials serve as the passport for your digital identity, authenticating users before they access various systems, applications, and data.
Organizations may include sophisticated or additional authentication methods to provide advanced information security. If the authentication process requires additional steps, it is referred to as “multifactor authentication” (MFA).
Standard methods pair a unique username with a password (“something you know”). Sophisticated authentication practices, such as MFA, require the user to also provide another factor of authentication. These additional factors can be a physical object (“something you have”) such as a key card or OTP token, or a part of the user’s body (“something you are”), such as a fingerprint, or a facial recognition scan.
IAM Authorization
Authorization carries out the rest of an organization’s identity and access management processes once the user has been authenticated. Users are granted authorizations according to their role at an organization. This practice is referred to as “role-based access control” (RBAC).
Authorizations determine a role’s resources and level of access in the network. These items may include systems, applications, file shares, printers, and more. For example, an accounting department employee who regularly works with payroll software must be authorized to do such. If authentication resembles a passport, authorizations are the things your digital identity can access with it.
While authentication is fairly straightforward, authorizations and their management are far more challenging. Authorizations consist of complex sets of rules, rights, groups, and permissions explicitly configured per user account.
IAM Systems
The core of Identity & Access Management (IAM) oversees all authentication and authorization processes. As such, IAM systems are valuable management solutions for all departments. IT may manage your authentications and authorizations, but your entire organization feels it if your access rights and processes are misaligned.
Identity and Access Management software streamlines the entire process of managing user accounts. This functionality consists of:
- Automatic User Provisioning
- Workflow Management and Self-Service
- Password Management
- Single Sign-On (SSO)
- Role-Based Access Control/Access Governance
- Audit & Compliance Requirements
Identity Governance & Administration (IGA) as the new term for IAM
There has been a shift towards using the more aptly-named Identity Governance & Administration (IGA) in place of IAM. This is because access governance delivers far more granular control over your environment than more traditional user administration and provisioning.
Gradually, the term change is being adopted by both industry and research organizations. Companies like Gartner now use IGA to describe solutions that offer both identity and access governance along with traditional user account lifecycle management across multiple systems.
Tools4ever is dedicated to IGA & IAM solutions
For over 20 years, Tools4ever has developed solutions dedicated to streamlining account management tasks. Our goal is to ensure our partners have the right software tools to manage their environments and processes. From managing identity and access controls to improving IT security to unburdening helpdesks worldwide, Tools4ever delivers quality IGA & IAM solutions.
What is Identity and Access Management? FAQ
What does automating IAM allow you to do?
Manual identity and access management requires significant time and effort to execute but remains prone to oversights, slow execution, and data entry errors. Manual provisioning also typically requires unnecessary administrator-level permissions for Tier 1 staff, inherently increasing security risks.
Automating IAM allows your organization to increase efficiency and security, virtually eliminate errors and delays, and reclaim significant IT bandwidth. By connecting your HR system to Active Directory (or another directory service), you can create, provision, and manage users/groups; assign role-based access; and secure your entire IT environment with rapid process execution over every user’s complete lifecycle—from onboarding to offboarding.
Once a user is provisioned, what happens when their role or their access requires changes?
Changing a user’s access rights can happen in a few different ways with an identity and access management system. If the user received a promotion or official position change, an established Access Governance model will automatically update (or “reprovision”) their rights according to role-based access control.
If the user’s access only needs to change for a temporary period (e.g., ad hoc projects), then self-service capabilities will allow them to request access or their manager to preemptively assign it.
What are “reprovisioning” and “deprovisioning”?
Reprovisioning occurs whenever an automated provisioning solution executes provisioning processes for existing users, updating their access rights to the most current for their role. If no access changes are necessary for the user at the time of scheduled execution, none will be made.
Deprovisioning is one of the many steps that must occur for safe user offboarding when an employee departs an organization. All of the user’s accounts and access rights must be removed and deactivated for secure and compliant operations. Deprovisioning should be regarded as part of an offboarding process for departing users.
What are “downstream resources”?
Downstream resources generally include all the various systems, applications, and data that users required provisioned access to after their Active Directory (or another directory service) account has been created.
What is “user onboarding”?
Simply put, “onboarding” refers to the process of getting a new hire up to speed on organizational processes, and policies, and with provisioned access to the necessary resources required for their job’s responsibilities. Successful onboarding aims to help new employees quickly become effective within the organization.
Tools4ever’s solutions optimize the business and IT side of onboarding processes that provision new users’ access to network resources like accounts, applications, and file shares.
