“Multifactor authentication” (MFA) is an account security process requiring two or more separate steps for a user to prove their identity. It most commonly refers to logging into a computer, network, application, or other resources. To complete a multifactor authentication process, you must provide specific credentials or meet certain conditions at each stage. While “two-factor authentication” remains a popular term, MFA has increasingly become the umbrella term.
People already use MFA processes to regularly prove their identities outside of IT scenarios. For example, an ATM card requires a personal identification number (PIN). Authentication only occurs when both the card and PIN are used together; they do not authenticate anything exclusive of each other.
Nearly everyone is familiar with the most common form of authentication in use today: username and password combinations. Since the creation of individual user accounts for computer and application access, usernames and passwords have been the norm.
In the United States, the average email address is associated with 130 different user accounts.i The vast majority of these user accounts require a username and password combination to log in. Two-thirds of users reuse passwords across multiple accounts, causing a chain effect if any of them are compromised.ii
More and more, cloud resources are adding additional authentication steps to traditional username and password prompts. Should the user’s username and password credentials be compromised, one would still need further information or means to log in. Single-use PIN (or a “one-time password”) or verification codes may be sent to users via text/SMS or email. Entering these unique values meets the additional authentication step. Online banking and personal finance apps make regular use of this MFA method, especially when users log in on new devices.
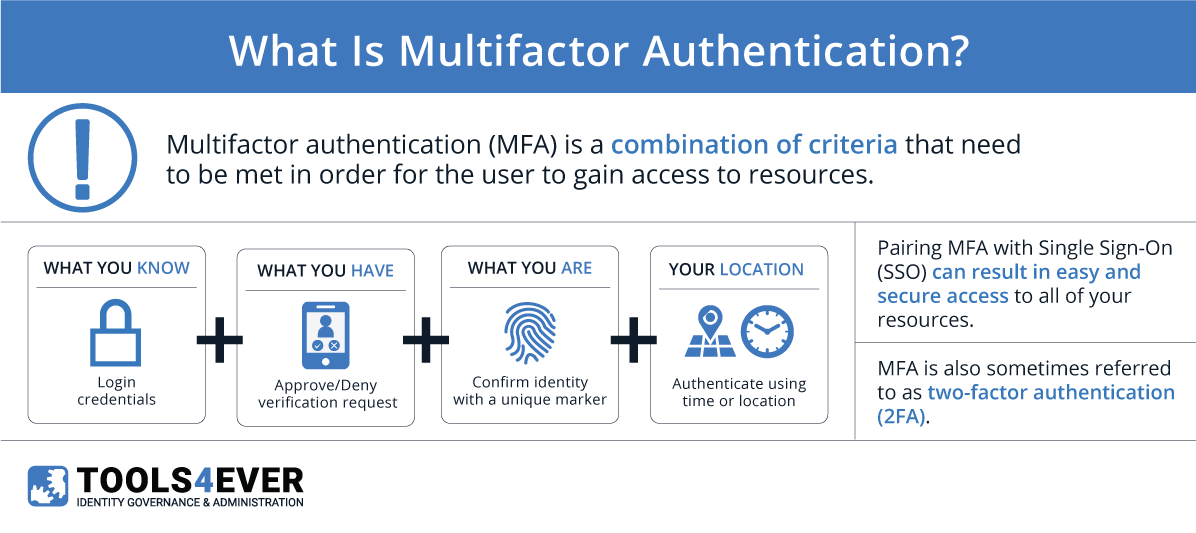
5 Authentication Factors
In the realm of authentication, a “factor” is something that can be used to verify a user’s identity. For example, a username and password combination is a single factor. MFA combines two or more factors in order to make the authentication process more secure. For each factor required for authentication, it becomes exponentially more difficult to impersonate a user. MFA may require two or more of the following factors:iii
Knowledge – refers to “something you know.” Knowledge is the most common credential factor used across authentication methods and includes a username and password combinations. Security questions that also require “something the user knows” are grouped with this factor as well. It should be noted that a username and password combination counts as a single factor. The same is true for a given series of security questions. Combining a username and password with a security question is still considered single-factor authentication since they both fall within this category.
Inherence – refers to “something you are.” This authentication factor includes all biometric data that could serve as credentials. Examples include fingerprints, DNA, facial recognition, and retina scans. This type of authentication has become increasingly popular with mobile devices that have built-in fingerprint scanners and facial recognition.
Possession – refers to “something you have.” Traditionally, items such as key cards and hardware tokens were held in the possession of users. One-time passwords sent via text/SMS or email to users’ mobile phones have been increasingly categorized under this factor. The use of mobile devices helps combat the risk of losing physical items like scanner cards. In some systems, the user’s device itself acts as a factor in this category, having been flagged as a “trusted device”.
Location – refers to any geographic or network restrictions that may be added to authentication methods for additional security. In addition to other factors, users must meet the location conditions configured for the given resource to be authenticated. For example, users may only access an application when they are inside your corporate network, or within a specific country.
Time – refers to any restrictions that may be added to keep authentication within a set range of hours. In this way, Time and Location factors are similar. Time-based factors provide security if your users never have reason to log in during certain periods—outside of 9 am-5 pm, for example.
Time- and location-based factors can be combined to make ever more strict conditions. False authentication attempts may occur within too close a window and from too far away to be legitimate. Three attempts to log in to Bob’s user account within a 10-minute window isn’t too suspicious. People mistype credentials all the time. However, it would be suspicious if those attempts originate from New York, Chicago, and Los Angeles within that same time period.
Everyday MFA
Identifying these authentication factors is pretty easy when we reconsider the context of the ATM card example. In order to withdraw money, you must first authenticate yourself. Your ATM card serves as “something you have” (Possession) and your custom PIN number is “something you know” (Knowledge).
Hypothetically, different factors or conditions could be enforced. Your ATM card could require a fingerprint instead of a PIN. MFA would still be enforced by swapping “something you know” for “something you are” (Inherence). If your bank restricts the number of ATM locations you had access to, a location factor is in effect. Limits on the transaction volume over the course of one day, enforce a Time factor.
While not enforcing MFA with every swipe, credit cards help provide use cases for why MFA is important. Credit companies freeze cards that have been used well outside the normal area of activity. This is similar to a passive Location factor or condition designed to prevent identity theft.
If Bob from New York suddenly has his card used a few times in Los Angeles, it may register as suspicious. You may be on vacation, but the outlying activity appears suspect. As a result, the account is automatically locked on the chance that your identity or card number were stolen. Attempting to authenticate in overly bizarre circumstances should surely raise red flags.
OTPs on the Rise
The combination of username and password credentials remains the most prevalent authentication method. While organizations easily recognize the importance of enhanced security, adding additional authentication factors used to be an expensive and time-intensive investment. Thanks to the creation of one-time passwords (OTPs) in recent years, this barrier to implementing MFA has largely disappeared. As a result, adoption is increasing. Application developers can easily add a possession factor to their authentication process by sending unique PIN codes to users’ phones or emails.
MFA adoption is also increasing because end users find it more intuitive and easier than ever. Free software clients are now available for use on mobile phones that generate OTPs for cloud resources supporting MFA.
OTP clients often set short windows of validity before changing the credential value. Google Authenticator’s OTP reset every 30 seconds, for example, severely minimizing the risk should a value be compromised. Increased security is only truly successful if the process is also straightforward and seamless. Today’s MFA is simple enough to sufficiently enforce tighter access without accidentally incentivizing workarounds.
The security MFA adds to your authentication processes makes it a no-brainer. With MFA, it’s more difficult for users to misuse their access rights and for malicious intruders to impersonate them doing so.
i. https://digitalguardian.com/blog/uncovering-password-habits-are-users-password-security-habits-improving-infographic
ii. https://www.infosecurity-magazine.com/news/google-survey-finds-two-users/
iii. https://searchsecurity.techtarget.com/feature/5-common-authentication-factors-to-know
