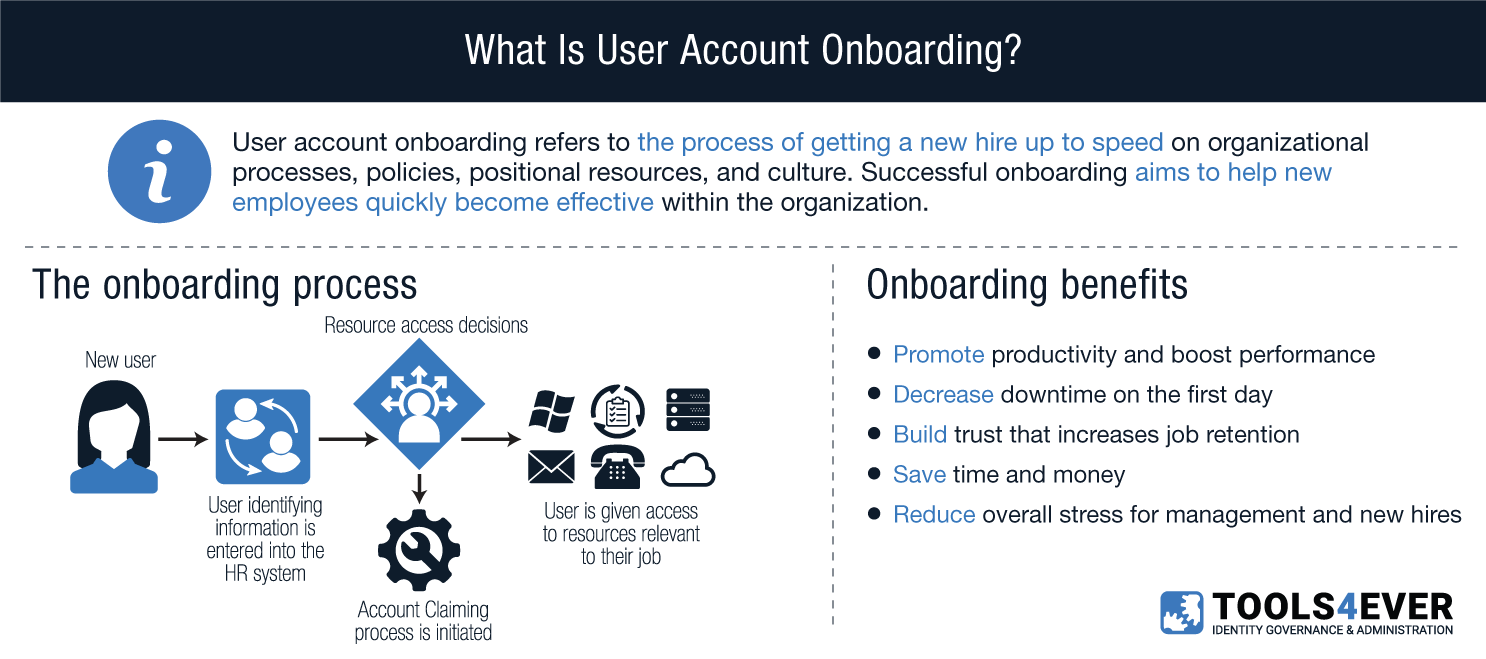
Simply put, “onboarding” is managerial jargon first used in the 1970s that refers to the process of getting a new hire up to speed on organizational processes, policies, positional resources, and culture. Successful onboarding aims to help new employees quickly become effective within the organization.
You could write whole books on the full scope of onboarding—people have if you’re into that sort of thing—but let’s stick to Tools4ever’s expertise on the IT side of this process. We specialize in optimizing the business and IT processes that ensure users’ access to network resources like applications and file shares.
Onboarding & Provisioning: Security
When a new employee starts a job that requires access to a computer or email, they’ll need an account—likely in Active Directory or Google G Suite. Some organizations create and provision all of these accounts and resources by hand, which takes a lot of time. Those who work with Tools4ever automate the process, and everything is created in a snap. Either way, once the new user accounts and passwords are set up, it’s time for the riskiest part of any onboarding plan: the hand-off.
The transfer of new user credentials is one of the largest vulnerabilities that exist in any organization’s security. Organizations with even the most sophisticated security and password policies are susceptible to this often-overlooked risk, despite Gartner reporting that information security spending will exceed $124 billion this year.i
Many organizations use an easily-deciphered default password formula when creating new accounts. For example, the first two letters of your first name, your birth year, and your last name may generate “St1986Smith”. If someone can recognize the formula, they can guess the password for a new account before that user gets to log in for the very first time. If some social engineering or a cursory Google and Facebook search can give you all the relevant details for an easily cracked password formula, can you really call it secure?
Some organizations even use the same default password for every single account generated for a new user (e.g. “Passw0rd123”). With that practice, it doesn’t matter if a malicious individual can crack your password formula or dig up some generic info. If everyone has the exact same password for their initial login, everyone in your organization knows what Bob’s password is before he gets a chance to show up at work and make a new one.
For all the good an 18-character passphrase and 30 days expiry does, the initial account creation stage is often the most vulnerable moment for any user account. In order to mitigate this risk, Tools4ever developed SSRPM’s Account Claiming module to protect the onboarding process without major IT overhauls.
SSRPM’s Account Claiming Module
With Account Claiming, new accounts are created in a disabled state and are associated with a unique “claim ID.” This claim ID can be something the employee already knows or can find in their onboarding documentation (e.g. their employee number).
You can now feel safe delivering that unique claim ID to the new user via intermediary or email when the time comes. The Account Claiming module and its web portal provide sufficient security so that knowing the claim ID alone is not enough to access the new account. If it is a value that the new user knows, you don’t even have to transfer the claim ID itself. Instead, you can further conceal the credentials by providing the knowledge of where to find the value at the appropriate moment (e.g. “input your employee number, which is found inside your ‘Welcome Folder’ on the left side”).
The new user simply enters the claim ID into SSRPM’s Account Claiming portal, accessed through the web or the Windows logon screen, and they are then challenged to further identify themselves. The new user provides specific, but non-sensitive information by answering challenge questions that your organization has configured for them. The Account Claiming module verifies whether the information matches. If the user is verified, their account is activated and they must change their password from the default one provided.
The new user now has everything they need to log in and begin their work on day one—and your organization has patched a massive security hole.
